NEWSLETTER

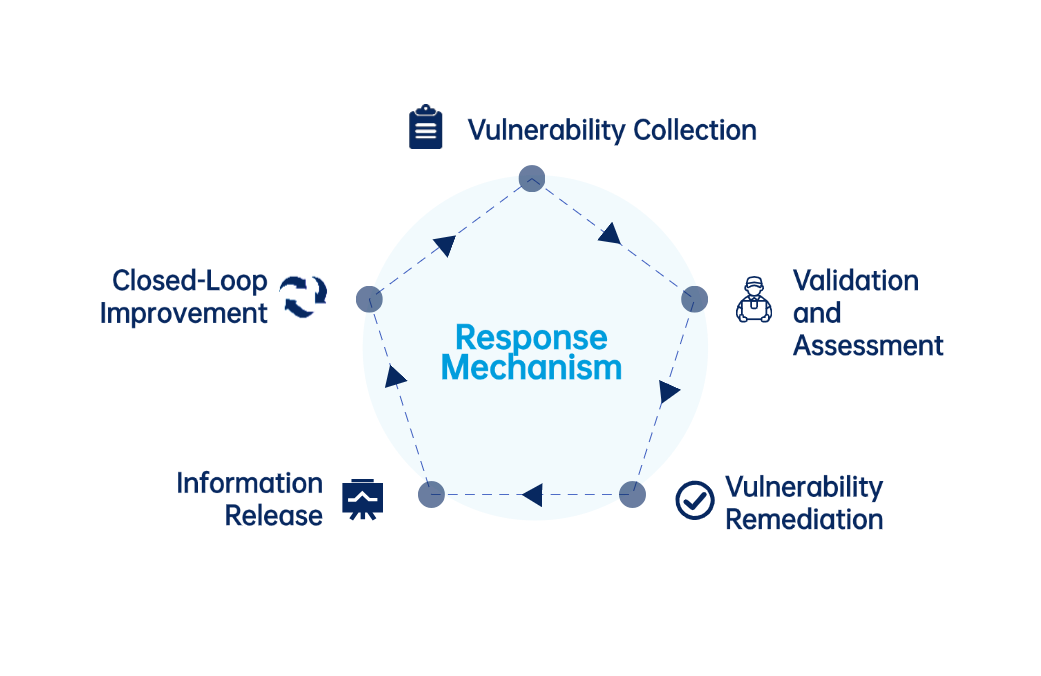
We are committed to building and implementing a comprehensive “End-to-End Global Cybersecurity Assurance System” as a key strategy for our company. Through robust policies, organizational structures, procedures, management practices, technologies, and standards, we have established a sustainable and reliable vulnerability management system. We encourage users, partners, suppliers, and others who discover potential security risks or vulnerabilities related to our products and solutions to proactively report them to us via email (service@senergytec.com). To facilitate the verification and identification of vulnerabilities, please include, but do not limit your report to, the following information in the email.
We will implement a strict vulnerability information handling process, limiting access to only those personnel involved in addressing the vulnerability. Additionally, we require individuals who report the vulnerability to keep it confidential until it is publicly disclosed.
We publicly disclose security vulnerabilities through the following two approaches:
Support Period: The device is actively maintained concerning security updates for the following 5 years after placing on the market.
Progress Updates: We will send an email confirmation within 24 hours of receiving your report and keep you updated on the progress.

